What You Need to Know When UpgradingEDI Environment to AS4 Protocol
Contributors

Most EDI environments still work. Messages flow, partners stay connected, and transactions complete. That apparent stability is exactly why many organizations delay upgrading. The problem is not visible failure. The problem is hidden risk.
As partner ecosystems expand and compliance expectations tighten, legacy EDI protocols are being pushed beyond what they were designed to support. Issues surface under pressure, not in day-to-day operations.
This is where AS4 (Applicability Statement 4) becomes relevant. Not as a technical refresh, but to bring more predictability, control, and transparency to business-critical integrations. This blog helps examine what AS4 changes, where its benefits are felt most, and why upgrades fail when approached without intent.
What is AS4?
AS4 is a modern standard for exchanging business data between organizations over the internet. It uses web services based on XML and SOAP and evolved from the XML framework to support secure digital business communication.
AS4 is widely adopted in current EDI and B2B integrations and is positioned as the successor to AS2, not because AS2 is broken, but because it was not designed for today’s scale, security expectations, and governance requirements.
At its core, AS4 introduces message-level control, not just transport-level security.
Why AS4 Exists: Designed for Today’s Integration Reality
AS4 was introduced because legacy EDI could no longer keep up with how businesses exchange data today. Its benefits are less about new capabilities and more about removing uncertainty from critical integrations.
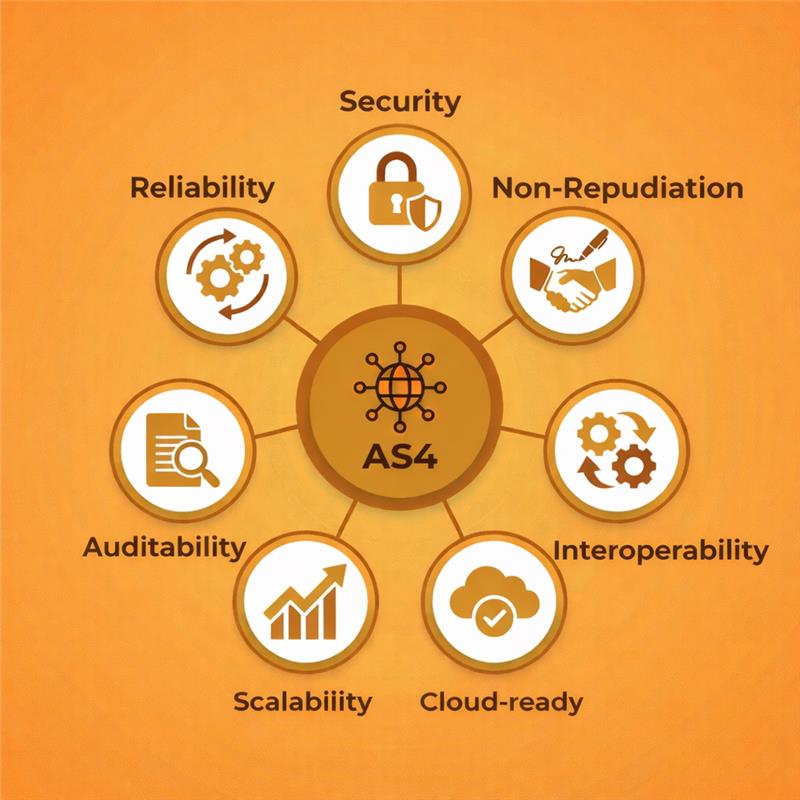
Here is what AS4 improves immediately:
- Messages are delivered once and only once, with explicit success or failure confirmation.
- Message-level protection ensures data remains private and unaltered from end to end.
- Both parties can conclusively prove message origin and receipt.
- Receipts and metadata create a clear, built-in audit trail.
- Standardized profiles reduce partner-specific integration efforts.
- Supports rising message volumes and expanding partner ecosystems.
- Aligns with cloud, hybrid, and distributed enterprise architectures.
| AS2 vs AS4: Operational Impact Comparison | ||
|---|---|---|
| Differentiators | AS2 | AS4 |
| Standard maturity | Widely adopted legacy standard | Modern standard, successor to AS2 |
| Architecture model | Point-to-point file transfer | Web services-based messaging |
| Transport mechanism | HTTP/HTTPS | Web services (SOAP over HTTP/HTTPS) |
| Message format | EDI payload over HTTP | XML-based messaging with structured metadata |
| Security approach | Transport-level security | Message-level security |
| Non-repudiation | Limited and implementation-dependent | Built-in non-repudiation |
| Reliable delivery | Basic acknowledgements | Guaranteed delivery with reliable messaging |
| Duplicate message handling | Limited and inconsistent | Explicit duplicate detection window |
| Receipt handling | Basic MDN acknowledgements | Multiple receipt types with clear delivery semantics |
| Interoperability | Partner-specific configurations | Standardized profiles improve interoperability |
| Scalability | Becomes complex as partners grow | Designed for large, distributed ecosystems |
| Cloud compatibility | Limited alignment | Designed to fit cloud and hybrid environments |
| Auditability | Fragmented logging and tracking | Receipt-driven audit trail |
| Error handling | Often manual and reactive | Structured error handling |
| Partner onboarding | Slower, custom-heavy | Faster, more predictable |
| Governance support | Difficult to standardize | Easier governance and monitoring |
Source: ANSI
Why AS4 Upgrades Fail Without Strategy?
AS4 upgrades fail when organizations underestimate what changes beneath the surface. AS4 introduces stricter requirements around security, reliability, and message handling, making infrastructure setup and testing significantly more demanding than legacy EDI.
Common failures stem from mismanaged certificates, incomplete agreement on AS4 profiles, weak error handling, and poor message tracking. Testing is often rushed, and cutovers happen without rollback plans, increasing the risk of disruption.
Beyond technology, adoption is slowed by resistance to change and uneven partner readiness. AS4 success depends on coordination across trading partners, not just internal systems.
When treated as a simple protocol upgrade, AS4 exposes complexity instead of reducing it. Without a deliberate, well-tested transition, failures are not a question of if, but when.
Conclusion: What Leadership Should Decide
AS4 adoption is no longer a technical preference. It is a leadership decision about how much operational, and compliance risk the organization is willing to carry as integration demands grow.
What leaders need to decide now:
- Risk posture: Is the current EDI environment defensible under rising message volumes, audits, and security scrutiny?
- Timing: Do you modernize your own terms or wait until partners, regulators, or incidents force the change?
- Control: Can legacy EDI provide the visibility, traceability, and accountability the business now expects?
- Execution model: Is AS4 approached as a governed, phased transition, or as a rushed upgrade under pressure?
AS4 provides a standardized, secure, and auditable exchange model that legacy EDI increasingly struggles to support consistently.
For many leadership teams, the challenge is not deciding whether AS4 makes sense but understanding how exposed the current environment is.
A short, objective review of your EDI posture can help surface blind spots, validate assumptions, and outline practical next steps before urgency removes choice. Sometimes, a second set of experienced eyes is all it takes to turn uncertainty into a clear path forward.
Other Popular Articles
In the digital age, businesses must adopt an ad
GRC is the capability, or integrated collection










