OT Ransomware Risks and Response for Industrial Systems

Production did not stop because systems failed. It stopped because access was lost.
That is how most operational technology (OT) ransomware incidents begin.
Many organizations still treat OT ransomware as an IT security issue. That mistake costs time, money, and control. In OT environments, ransomware is an operational event first.
This blog is written for leaders responsible for keeping plants running. That includes operations leaders, plant managers, OT and IT security teams, and risk and compliance owners who support industrial environments.
Learn why OT environments face higher ransomware risk, how attackers gain access, and how detection should work during incidents. The goal is simple: help leaders spot risk early and reduce impact when it matters most.
Understanding OT Ransomware
OT ransomware is a malicious software that disrupts industrial operations. It targets systems used to run and monitor physical processes, including Industrial Control Systems (ICS), Supervisory Control and Data Acquisition (SCADA) systems, Human Machine Interfaces (HMIs), and Programmable Logic Controllers (PLCs).
In traditional IT environments, ransomware blocks access to data.
In operational technology environments, the impact is different. Ransomware disrupts process availability and operational visibility, even when control logic and equipment remain intact.
Why is OT so Susceptible to Ransomware?
The top five reasons that heighten the risk of ransomware in OT environments are:
- IT-OT Convergence Risks
IT and OT networks are increasingly connected, but security lags. Once attackers compromise IT systems, weak segmentation lets them move into OT environments. Often, this lateral movement remains undetected until it disrupts operations.
- Uncontrolled Remote Access
Remote access expanded rapidly after the pandemic. Security controls did not keep up. Weak credentials and limited monitoring make remote connections one of the fastest entry points into OT environments.
- Legacy Systems Under Modern Exposure
Many legacy ICS devices use protocols like Modbus and DNP3 that were designed without encryption or authentication mechanisms, making them inherently vulnerable to modern attack techniques.
- Limited OT Visibility
OT networks often lack consistent monitoring. This creates blind spots in asset inventory and network traffic. Traditional IT security tools do not work well in OT environments. They cannot interpret industrial protocols such as Modbus. As a result, ransomware activity often goes unnoticed until operations are disrupted.
- High Cost of Downtime
OT ransomware often forces full plant shutdowns. Every minute of downtime results in direct production loss. Safety requirements can require complete stops during incidents. This increases financial impact and can trigger regulatory and supply chain consequences.
OT Ransomware Infection Vectors in Industrial Environments
OT ransomware enters industrial environments through a small number of repeatable paths. These paths fall into two groups. Direct attacks target OT systems, while indirect attacks come from IT environments.
Direct Attack | Indirect Attack |
|
|
Advanced Threat Actor Capabilities
Recent threat intelligence reveals that certain advanced persistent threat (APT) actors have demonstrated the capability to gain full system access to multiple ICS/SCADA devices, including:
- Schneider Electric programmable logic controllers (PLCs)
- OMRON Sysmac NEX PLCs
- Open Platform Communications Unified Architecture (OPC UA) servers
These actors can upload custom malicious agents to PLCs, enabling file manipulation, packet captures, and code execution via HTTP/HTTPS.
Basic Steps for OT Ransomware Detection
OT ransomware detection succeeds when teams focus on containment, sequence, and operational context. The following steps reflect how effective detection unfolds in OT environments.
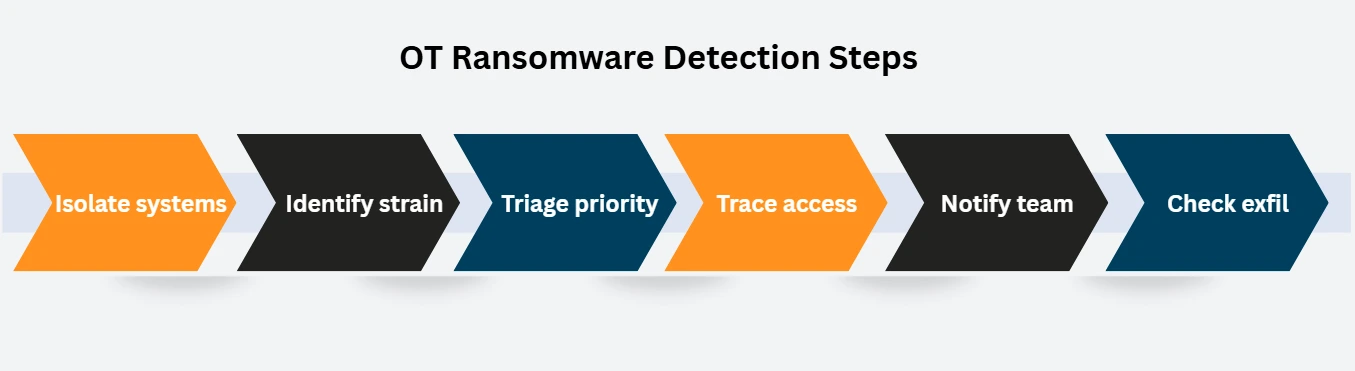
- Identify impacted OT- and OT-adjacent assets and contain them immediately. Early isolation limits spread and reduce damage.
- If isolation is not possible, shut systems down in a controlled way. Preventing further disruption is a priority.
- Determine whether the attack started in IT systems, remote access, or OT-facing assets. This helps close the right gaps.
- Prioritize systems based on safety and production impact. Not all assets carry the same risk.
- Identify how the ransomware spreads and encrypts systems. This informs recovery decisions.
- Assume data theft until proven otherwise. Early confirmation guides legal and communication steps.
From Insight to Action
These risks become easier to manage when viewed through real operational incidents.
This month, we are hosting a webinar for senior leaders focused on ransomware risk across plant and office environments.
The session will cover:
- Real ransomware cases from manufacturing and industrial settings
- How AI and automation are shaping detection and response across IT, OT, and IoT
- Governance and security practices that reduce downtime
- Response and recovery decisions during active incidents

Key Takeaways for Managing OT Ransomware Risk
OT ransomware is not a rare cyber issue. It is an operational problem driven by downtime pressure and slow detection. Most incidents follow known paths through IT systems, remote access, and trusted connections.
Better outcomes come from prompt action. Fast containment, clear sequencing, and shared ownership across IT and operations matter more than adding new tools.
This blog explains how ransomware enters OT environments and how detection should work. You can also explore our blog on ransomware prevention best practices to see how organizations reduce impact and respond with more control and confidence.
Other Popular Articles
In the digital age, businesses must adopt an ad
GRC is the capability, or integrated collection










