Cybersecurity Services
As you drive your business with Digital Transformation, we help make it Cyber Resilient across IT, OT, IoT, and People.

Overview
Risk and Cybersecurity Services
Defending and recovering from Cyberattacks has become a key part of business operations. Based on the industry, the IT, OT, and IoT need cyber protection. Information Technology (IT) includes Network Infrastructure, Cloud Infrastructure and Software Development whereas OT and IoT (Operational Technology & Internet of Things) include Manufacturing Plants, Power Grids, Utilities Pipeline, Hospitals, and more.
DivIHN helps protect its Enterprise, Public Sector, Education Institutions, and SMBs (small to medium business) through its Cyber Governance, Architecture, and Monitoring expertise.

Advisory
Advisory
Our customers, in any industry and of any size, engage with the best-in-class executive advisors from our CoE. Our Digital, Risk, and Cybersecurity Center of Excellence (CoE) serves as a Think-Tank to create a firm action backed by solid expertise. The customers benefit from the thought-capital we bring to sharpen their big-picture vision, strategies, execution plans, budgets, delivery roadmaps, team skills, and technology stack
Outcomes include:
- Actionable Board-Room Material for CISOs
- Enhancement(s) in customer’s cybersecurity posture strategies
- Single Version of Truth from a multitude of assessment reports (NIST, ISO, Privacy, Regulatory, etc.)
- Business Executive-facing Cybersecurity Risk, Resilience, and Response strategies
Services include:
- CISO Partner – Board, M&A, Strategic Think-Tank Help
- Rationalize Multiple Assessments
- Cybersecurity Program Design, Planning, and Implementation
- Cyber Educations for Business Executive (including Ransomware Tabletops)
Assessments
Assessments
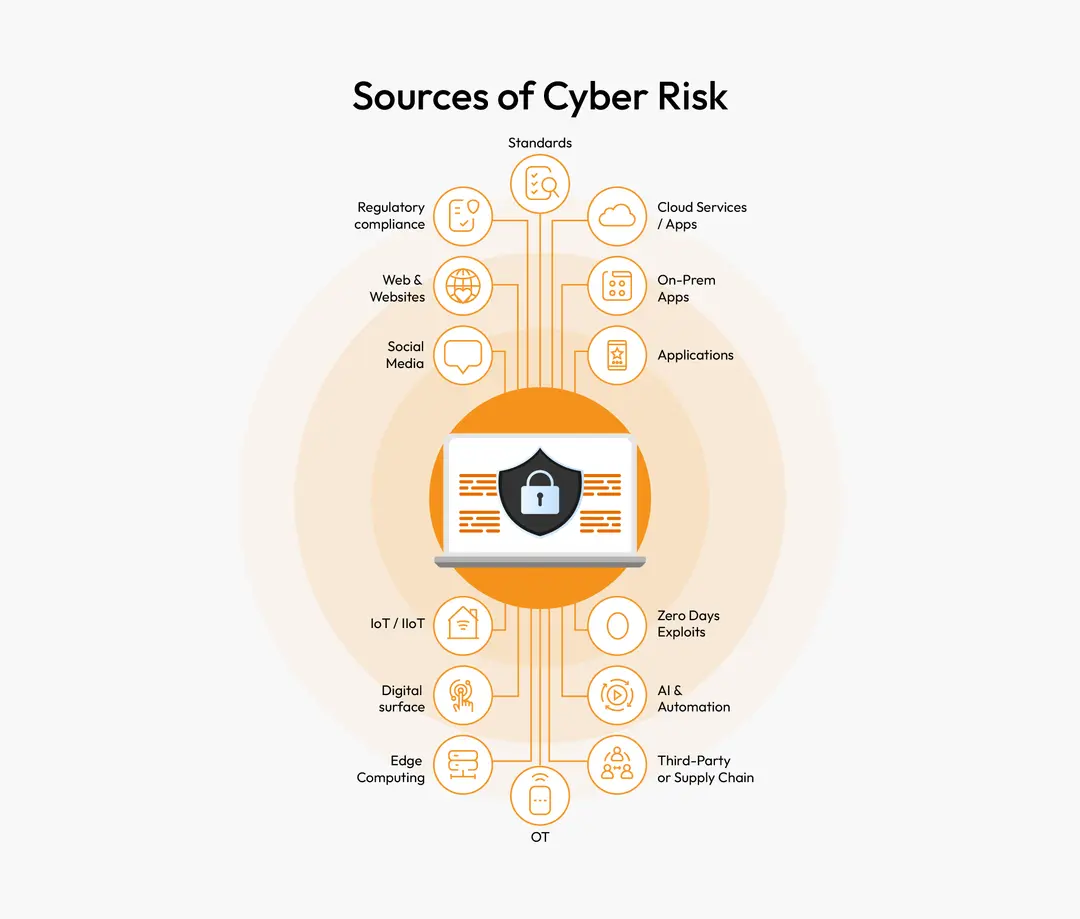
We emphasize on a dual approach of assessing the cybersecurity risks, namely, the impact on business as well as to comply with regulations and standards. We start with identifying the sources of risks (see below), and provide a fit-for-purpose assessment to propose a prioritized set of actionable strategies and roadmaps.
Outcomes include:
- Cybersecurity Risk Score and Gaps
- Remediation Roadmap and Budget Planning
Services include:
- Cyber Posture Assessments (CIS, ISO, NIST, SOC 2, etc.)
- Baseline Assessments
- Deep-Dive Assessments
- Consolidation / Rationalization of Multiple Risk Assessments

Implementation
Implementation
We work with our customers to implement cybersecurity portfolios, programs, and projects of various size and scope. A CISO entrusts us with implementing GRC programs (from policy design to education), hiring talent, deploying cybersecurity products (SaaS/On-Prem), as well as cyber operations programs, such as Incident Response & Management, Vulnerability Management, etc.
Outcomes include:
- Steady-state Cyber Programs
- Installed cyber products with proper configuration
Services include:
- Cyber Program/Project as per prioritized roadmap
- Cyber Project Implementation
- Cyber Security Product Implementation
Remediation
Remediation
Customers ask DivIHN to provide the remedies, mainly based on the recommendations and roadmaps delivered during the assessments. Remediations largely focus on filling the gaps in existing programs/practices, however, they could morph into a full-scale implementation as well, based on the nature of the recommendation from the cyber assessment.
Outcomes include:
- Fine-tuned cyber programs/products – with gaps remedied
- Increased effectiveness of cybersecurity posture and goals
Services include:
- Program Remediation
- Product (SaaS)/Configuration Remediation (e.g., Firewall)


Operations
Operations
Cybersecurity Operations include a combination of active or passive defense in either continuous or intermittent manner.
Outcomes include:
- First-responder treatment of cyberattacks
- Stronger cyber-posture through integration of various cybersecurity technologies like SOC, SIEM, XDR, AI/ML, SOAR, etc.
Services include:
- Security Operations Center (SOC)
- Penetration Testing: Network, Application, Website, IoT etc.
- Red/Blue/Purple Teaming
- Managed Security Services Provider (MSSP)
Special Projects
Special Projects
A Special Project is a service that does not conform to any of the standard services, namely, Advisory, Assessment, Implementation, Remediation, and Operations. Key examples include Cyber PMO (Project Management Office), BCP-DR, M&A, Innovation, Skill-Development, etc.
Outcomes include:
- Fit-for-purpose deliverables based on the scope of the special project, e.g., M&A
- Cyber-innovations within CISO Team
Services include:
- Mergers & Acquisitions-related (M&A) Cybersecurity Services
- Exploratory and Confirmatory Due Diligence
- Cyber-products integration & separation (for Divestitures)

Differentiator summary
We bring fit-for-purpose, customer-centric delivery strategies to align with customers’ business requirements, priorities, and budget sensitivities. This results in formulating strategically sound cybersecurity and risk-resilient postures.









