Last month, I introduced Systemic Digital Risk in Complex Digital Environments.
Systemic Digital Risk in Complex Digital Environments
I shared the view that Systemic Risk is the threat that component failure in a complex system will cascade and jeopardize the much larger system, and identified five elements of systemic risk that can significantly impact eight digital domains that work together across complex digital systems to produce and preserve business value. These lead us to new models for Integrated Risk Management … the DIRECTOR™ and RISCX™ frameworks (Source: “Systemic Digital Risk: Understanding and Overseeing Complex Digital Environments with The DiRECTOR™ And RISCX™ Frameworks”, Digital Directors Network. Used with permission).
The DiRECTOR™ framework shows us eight key domains that enable complex digital systems. From a corporate director’s perspective these domains represent the key risk areas within a business’s digital system. The domains are co-dependent and influence / control how a digital business system functions and supports business value.

Data: Digital systems create, store, process, update, and use data to create knowledge, insight, and business process action.
iArchitecture: Information architecture is the technical design spine of digital systems. Information architecture defines how information and digital systems interact within a business and between businesses. Information architecture enables all components of a digital system to interact – software, data, people, processes, networks, hardware.
Risk Communication: Leadership communication concerning strategic and tactical assessment, forecasting, planning and engagement of business and digital risk with all stakeholders, internal and external are key to protecting business value.
Emerging Technology: All emerging technologies possess the ability to enable, threaten or redefine existing business value drivers. As new technologies are engaged and applied anywhere across a business’s value chain, new complexities and risks emerge and must be accounted for.
Cybersecurity: Wherever there is business value, bad actors will attack to find the weakest links in a digital system and seek to take advantage for their own gain. This reality places constant strain on digital systems, creating significant value protection and preservation challenges from people to technology, internally and externally.
Third-Party: No business is an island. Every modern business, small or large, operates within a value chain of digital system inter-connecting other parties – Customers, Suppliers, Own Business operations. Extended businesses, digital systems and value chains are constantly connected and in motion creating inter-dependencies which can compound cascading contagion risk across all digital systems.
Operation of IT: Change is the one constant in digital systems and information technology. The ability of a business organization and its digital operations to effectively adapt to this dynamic is critical to the health, sustainability, and resiliency of a business’s digital system.
Regulation: Digital regulation is accelerating and expanding. Compliance is a boardroom staple and understanding how emerging regulations impact digital risk and security is required to shape responsible digital governance and policy formulation.
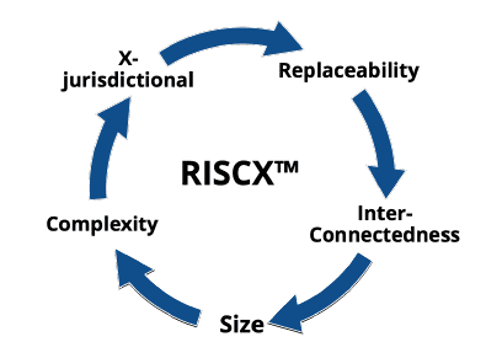
The RISCX™ framework presents for us five drivers of risk which are unique to today’s massively complex and interconnected digital system. Traditional risk management frameworks and assessment models often fail to consider and address these unique drivers of risk which have been seen to be the cause of systemic risk contagion on a massive scale.
Replaceability: How rare, irreplaceable, and important is a component within a complex digital system? Critical hard to replace components create significant risk and brittleness in complex systems. The more dependent a digital system is on a component, and the harder it is to replace or bring back to operational use if it fails, the greater the level of risk to the larger system.
Interconnectedness: Our digital systems and business processes have never been more interconnected than they are now. Complex digital systems are highly connected both internally and externally. The more interconnection points across a system, both inbound and outbound, the greater the risk that a failure can spread and cascade. This is the highest systemic risk trigger for contagion risk in the event of cybersecurity attacks, allowing failures to spread and cascade.
Size: Size impacts total exposure across complex digital systems. Size factors include size of the data universe enabled by a digital system; number of end-users; number of third and fourth parties; number of interconnect digital systems; number of business entities involved and providing digital systems in extended value chains; number of digital system providers contracted (both software licensed, SaaS and Cloud). Scale creates more points of vulnerability, adds to digital complexity, and contributes to increased digital systemic risk.
Complexity: Complexity in any environment makes it more difficult to understand how an environment functions and how it can be controlled. Digital complexity develops from multiple areas. These include the number of component elements and heterogeneity within the system and its operations. As the complexity of a digital system increases, so does the systemic risk to the digital system.
X-jurisdictional: The more regulatory environments a digital system is exposed to and must comply with, the more difficult it is to oversee and manage regulatory risk. Jurisdictions include regulatory bodies and other policy jurisdictions such as rules imposed by third parties.
In my next post I will discuss the integration of the DiRECTOR™ and the RISCX™ frameworks to provide a more comprehensive approach to assessing risk which I believe is needed to better appreciate and understand the unique systemic risks our business face in our complex digital world.
Note:
Source Material for this post- “Systemic Digital Risk: Understanding and Overseeing Complex Digital Environments with The DiRECTOR™ And RISCX™ Frameworks”, Digital Directors Network.
Joseph F. Norton is a Risk, Security, and Crisis Management professional.
He is a founding member and Qualified Technology Executive of the Digital Directors Network, Chair of the Advisory Board with Next Era Transformation Group, and Chief Security Officer with APF Technologies.
He has served as Chief Security Officer, SVP at Atos, Chief Technology Officer and Head of Operations, SVP at Philips, Chief Technology Officer, SVP at Novartis, Executive-in-Residence with McKinsey & Company, and Chief Technology Officer at McDonald’s. He has also held professional roles during his career with JPMorgan Bank, Oracle, Sybase and Grumman Aerospace Corporation, and the United States Navy.
DISCLAIMER
Copyright ©2023 by DivIHN Integration Inc. | [email protected].




