In my last post we examined the Risk Manager role we each play in our daily lives, as well as in our professional lives. Seems simple, doesn’t it?
From the Moment we are Born, we are Confronted by Risks
We survive from Birth because someone is Managing Risks to Protect Us
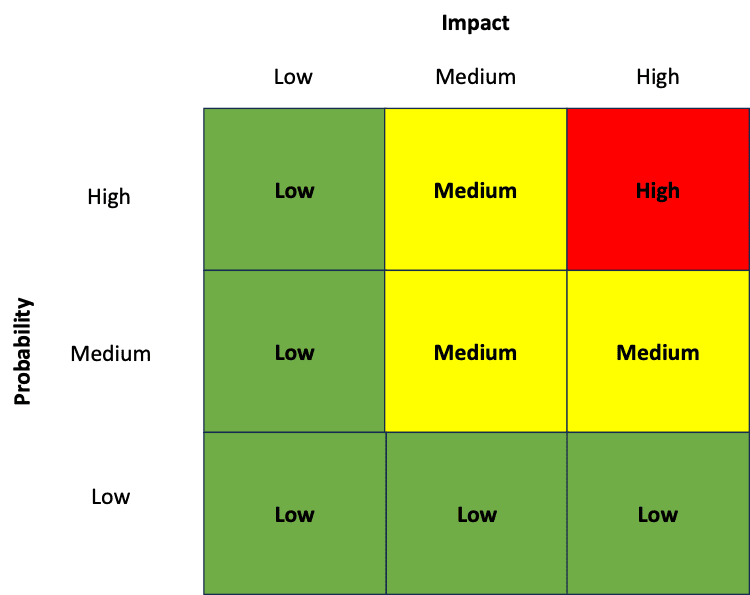
In business, we have audit departments and others who assess risks, and we engage in supporting risk assessments. One of the annual rights of passage for any business and information technology group is participating in the annual risk assessment process and the production of the Annual Risk Report. As cybersecurity professionals and business leadesr we may even present the results of our risk assessment to the company’s Board of Directors Audit Committee. A significant amount of time, effort, thought, and angst goes into creating these reports and presentations. We even become experts at preparing and interpreting classic management consulting 9X or 3×3 frameworks to map risks against Impacts and Probability. You may even use more sophisticated frameworks. Each of our traditional risk assessment frameworks ask us to identify risks, determine the potential impact of an identified risk, and also to assess a risk’s potential to occur or probability of occurrence. Using these graphical frameworks, we then plot individual risk and or categories of risk into an assessment box which labels a risk as low, medium, or high.
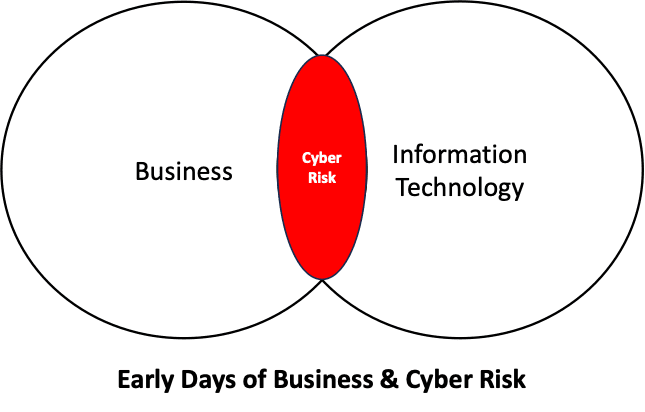
In the early days of formally assessing the intersection of business and cyber risk, the actual and perceived cyber risks were few and easily recognized. Pre and post the advent of the internet and today’s hyper-connected word, being hacked or suffering a data loss of intellectual property of personal identifying information were almost unheard of. The largest risks we would usually identify were related to information technology operations down time and the impact on business operations.
Today, however, the infusion of information technology into every aspect of our business, the interconnectedness of our business operations with hyper-connected suppliers, distributors, customers, and layers of third and fourth parties, spanning the world, has massively increased the Business / Cyber Risks we face.

I believe that the ways we have assessed Risks to our Business in the past are no longer adequate to address the complex nature of the web of risks we now face. Simple low, medium, and high-risk assessments no longer suffice to inform our business leaders and board members about the true nature of cyber driven risks.
Systemic Digital Risk in Complex Digital Environments
Systemic Risk is the threat that component failure in a complex system will cascade and jeopardize the much larger system. Systemic risk is inherent in all modern digital business environments. Systemic risk has become more prevalent as digital disruption and transformation advance throughout every aspect of business planning and operations, as well as in every aspect of society. The ability of organizations to create, capture and preserve value in rapidly changing digital economic systems makes understanding systemic digital risk a priority for all business leaders and boardroom members.
There are eight digital domains that work together across complex digital systems to produce and preserve business value.
- Data
- Information architecture
- Risk Communications
- Emerging Technology
- Cybersecurity
- Third Parties
- IT Operations
- Regulations
These eight domains enable complex digital businesses. They work in integrated relationships of people, processes, and digital systems to produce and preserve value. In traditional risk assessments we would identify risks within each of these domains, without necessarily fully appreciating the potential for individual domain risks to directly impact other domains.
Systemic Risk in complex digital businesses is primarily caused by five elements which impact these domains. These five key systemic risk causes are:
- Replaceability
- Interconnectedness
- Size
- Complexity
- Cross or X-Jurisdictional
I believe it to be imperative for business oversight to understand and comprehend risk within each of the eight domains of complex digital businesses and their systems, in conjunction with the compounding nature of Systemic Risk generated by the five key elements of systemic dependencies between and among these domains.
Any of the five key elements of Systemic Risk has the potential to trigger cascading contagion risk throughout and across not just a single business, but across every connected business in today’s complex customer-business-supplier value chains.
In my next post I will expand upon this introduction to Systemic Digital Risk and lay a foundation to deep dive into Cybersecurity Driven Risks and the five key elements of Systemic Risk.
Note: Source Material for this post- “Systemic Digital Risk: Understanding and Overseeing Complex Digital Environments With The DiRECTOR™ And RISCX™ Frameworks”, Digital Directors Network.
Joseph F. Norton is a Risk, Security, and Crisis Management professional.
He is a founding member and Qualified Technology Executive of the Digital Directors Network, Chair of the Advisory Board with Next Era Transformation Group, and Chief Security Officer with APF Technologies.
He has served as Chief Security Officer, SVP at Atos, Chief Technology Officer and Head of Operations, SVP at Philips, Chief Technology Officer, SVP at Novartis, Executive-in-Residence with McKinsey & Company, and Chief Technology Officer at McDonald’s. He has also held professional roles during his career with JPMorgan Bank, Oracle, Sybase and Grumman Aerospace Corporation, and the United States Navy.
DISCLAIMER
Copyright ©2023 by DivIHN Integration Inc. | [email protected].




